IDES Data Preparation
The International Data Exchange Service (IDES) is a secure managed file transfer service that allows financial institutions and tax authorities to securely send information on financial accounts held by U.S. taxpayers in accordance with the Foreign Account Tax Compliance Act (FATCA). Files transmitted via IDES must be encrypted and packaged in accordance with published data preparation instructions. The data preparation process is an important step to ensure that information transmitted via IDES conforms to U.S security standards to safeguard sensitive information.
The IDES Data Preparation OpenSSL project repository demonstrates the commands necessary to decrypt notifications downloaded from the IDES portal. The included commands are Windows specific, Linux specific, and a process that includes manual editing that will work for those and other systems.
The sample commands are intended to be run from a batch file located along with the OpenSSL executable, the Key and Payload files from the notification, and the receiver's private key.
Please note that there are many open market tools that produce the same results; however, the IRS does not endorse any commercial products, including the frameworks used in the example.
CBC Encryption - Windows Batch Scripting
The following code should be placed into a batch file and run in the same folder as the openssl executable.
The following files are required and the filename in the batch script will need to be replaced with your filename for each:
cbctest_public.pem - This will be the IRS Public Key for upload into IDES. A copy of this test key is included in the repository for testing these commands. The .p12 this was created from is included as well with a password of "password".
PAYLOAD.ZIP - This is the Payload file that will be uploaded to IDES
A random 48 byte value will be created that will be used to create the AES key and the IV. The first command will encrypt the Payload and will use parsed values from the random 48 byte value. The second command will encrypt the 48 byte value that contains the AES key and the IV. The output from these commands will be the encrypted Payload and the encrypted Key file.
setlocal enabledelayedexpansion
openssl rand 48 > 48byterandomvalue.bin
hexdump /bare 48byterandomvalue.bin > 48byterandomvalue.txt
set /a counter=0
for /f "tokens=* delims= " %%i in (48byterandomvalue.txt) do (
set /a counter=!counter!+1
set var=%%i
if "!counter!"=="1" (set aes1=%%i)
if "!counter!"=="2" (set aes2=%%i)
if "!counter!"=="3" (set iv=%%i)
)
set result1=%aes1:~0,50%
set result1=%result1: =%
set result2=%aes2:~0,50%
set result2=%result2: =%
set aeskey=%result1%%result2%
set initvector=%iv:~0,50%
set initvector=%initvector: =%
openssl aes-256-cbc -e -in PAYLOAD.zip -out PAYLOAD -K %aeskey% -iv %initvector%
openssl rsautl -encrypt -certin -inkey cbctest_public.pem -in 48byterandomvalue.bin -out 000000.00000.TA.840_Key
Running the batch file:
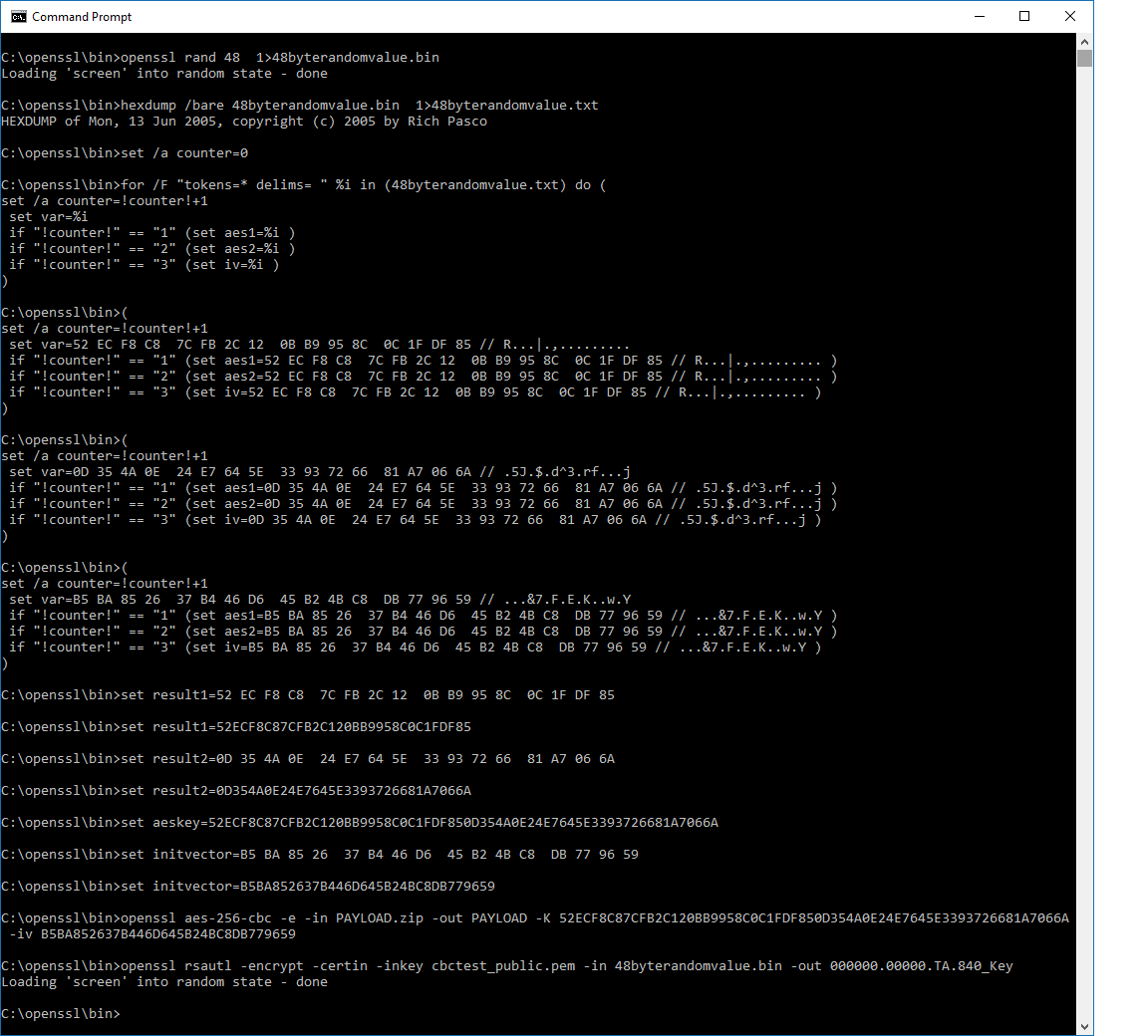 Figure 1
Figure 1
CBC Decryption - Windows Batch Scripting
The following code should be placed into a batch file and run in the same folder as the openssl executable.
The following files are required and the filename in the batch script will need to be replaced with your filename for each:
KEYFILE - this is the Key file that will be in the downloaded notification .zip file, 000000.00000.TA.840_Key for example
cbctest_private.pem - This will be your private key that corresponds to the certificate that was uploaded into IDES. A copy of this test key is included in the repository for testing these commands. The .p12 this was created from is included as well with a password of "password".
PAYLOAD - this is the Payload file that will be in the downloaded notification .zip file
The first command will decrypt the 48 byte value which contains the AES key and the IV. The batch code will parse the hex values of the AES key and IV to prepare it for the second command. The second command will use the AES key and IV in hex format and decrypt the Payload file. The output will be the decrypted Payload .zip file.
setlocal enabledelayedexpansion
openssl rsautl -decrypt -hexdump -in KEYFILE -inkey cbctest_private.pem -out aeskeyandiv.txt
set /a counter=0
for /f "tokens=* delims= " %%i in (aeskeyandiv.txt) do (
set /a counter=!counter!+1
set var=%%i
if "!counter!"=="1" (set aes1=%%i)
if "!counter!"=="2" (set aes2=%%i)
if "!counter!"=="3" (set iv=%%i)
)
set result1=%aes1:~7,48%
set result1=%result1: =%
set result1=%result1:-=%
set result2=%aes2:~7,48%
set result2=%result2: =%
set result2=%result2:-=%
set aeskey=%result1%%result2%
set initvector=%iv:~7,48%
set initvector=%initvector: =%
set initvector=%initvector:-=%
openssl aes-256-cbc -d -in PAYLOAD -out PAYLOADOUT.zip -K %aeskey% -iv %initvector%
Running the batch file:
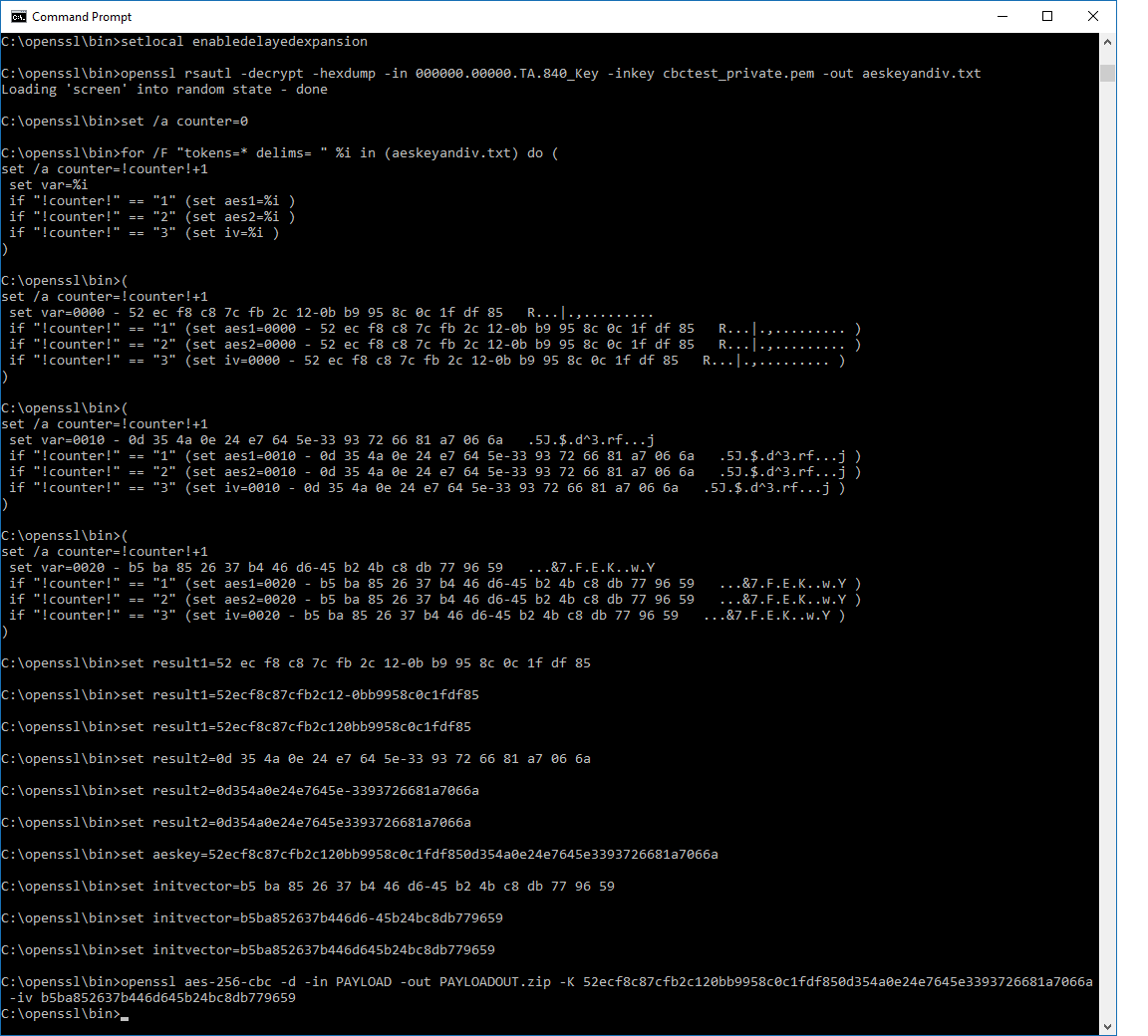 Figure 1
Figure 1
CBC Encryption - Linux Shell Scripting
Similar to the Windows method above, the following code should be placed into a shell script and run in the same folder as the openssl executable.
The following files are required and the file names passed to the batch script will need to be replaced with your filename for each:
RECEIVER_PUBLIC_KEY - This will be the IRS Public Key for upload into IDES. A test key for this has been included in the repository. SENDER_PAYLOAD_IN - This is the Payload file that will be uploaded to IDES ENCRYPTED_PAYLOAD_TO_SEND_OUT - This is the name of the encrypted Payload file that will be created ENCRYPTED_AES_IV_TO_SEND_OUT - This is the name of the encrypted Key file that will be created
#!/bin/bash
#
# @author Subir Paul (IT:ES:SE:PE)
#
#
SCRIPT=$0
function usage {
printf 'Usage: %s -pubkey <receiver public key pem input file> -in <plain text input file> [-aeskeyiv <encrypted aeskey+iv output file>] [-out <cipher text output file>\n' $SCRIPT
exit 1
}
if [ $# -le 1 ]; then
usage
fi
# Reset all variables that might be set
INFILE=
OUTFILE=
PUBKEY=
AESKEYIV=
# Read command line args
while :; do
case $1 in
-h|--help)
usage
;;
-in|--in)
if [ -n "$2" ]; then
INFILE=$2
shift
else
printf 'ERROR: "-in" requires a non-empty option argument.\n' >&2
exit 1
fi
;;
-pubkey|--pubkey)
if [ -n "$2" ]; then
PUBKEY=$2
shift
else
printf 'ERROR: "-pubkey" requires a non-empty option argument.\n' >&2
exit 1
fi
;;
-aeskeyiv|--aeskeyiv)
if [ -n "$2" ]; then
AESKEYIV=$2
shift
fi
;;
-out|--out)
if [ -n "$2" ]; then
OUTFILE=$2
shift
fi
;;
--) # End of all options.
shift
break
;;
-?*)
printf 'WARN: Unknown option (ignored): %s\n' "$1" >&2
;;
*) # Default case: If no more options then break out of the loop.
break
esac
shift
done
if [ -z "$PUBKEY" ]; then
printf 'missing -pubkey <receiver public key pem input file>\n'
usage
fi
if [ ! -f $PUBKEY ]; then
printf 'missing receiver public key input file %s\n' $PUBKEY
exit 1
fi
if [ -z "$INFILE" ]; then
printf 'missing -in <plain text input file>\n'
usage
fi
if [ ! -f $INFILE ]; then
printf 'missing plain text input file %s\n' $INFILE
exit 1
fi
if [ -z "$OUTFILE" ]; then
OUTFILE=`echo $INFILE.out`
fi
if [ -z "$AESKEYIV" ]; then
AESKEYIV=`echo $INFILE.aeskeyiv`
fi
echo "pubkey=$PUBKEY infile=$INFILE aeskeyiv=$AESKEYIV outfile=$OUTFILE"
# Create 32 bytes random AES key
TMP=`openssl rand 32 -hex`
AESKEY=`echo ${TMP:0:64}`
# Create 16 bytes random Initialization Vector (IV)
TMP=`openssl rand 16 -hex`
IV=`echo ${TMP:0:32}`
# Encrypt payload with key AESKEY and iv IV
openssl enc -e -aes-256-cbc -in $INFILE -out $OUTFILE -K $AESKEY -iv $IV
# Concatenate 32 bytes AESKEY and 16 bytes IV
TMP=`echo -n $AESKEY$IV`
# Convert AESKEY+IV hex to binary
AESKEYIVBIN=`echo $AESKEYIV.bin`
echo -n $TMP|perl -pe '$_=pack("H*",$_)' > $AESKEYIVBIN
# Encrypt aeskey_iv.bin with receiver's RSA PKI public key
openssl rsautl -encrypt -out $AESKEYIV -pubin -inkey $PUBKEY -in $AESKEYIVBIN
#delete AESKEYIVBIN
if [ -f $AESKEYIVBIN ]; then
rm -f $AESKEYIVBIN
fi
# Check if OUTFILE and AESKEYIV are created
if [ -f $OUTFILE ] && [ -f $AESKEYIV ]; then
echo "Cipher text payload file=$OUTFILE and aes key file=$AESKEYIV created"
fi
An example of running the script with the required parameters:
decrypt.sh privatekey.pem 000000.00000.TA.124_Key 000000.00000.TA.840_Payload 000000.00000.TA.840_Payload.zip
CBC Decryption - Linux Shell Scripting
Similar to the Windows method above, the following code should be placed into a shell script and run in the same folder as the openssl executable.
The following files are required and the file names passed to the batch script will need to be replaced with your filename for each:
RECEIVER_PRIVATE_KEY - This will be your private key that corresponds to the certificate that was uploaded into IDES. A copy of this test key is included in the repository for testing these commands. RECEIVED_ENCRYPTED_PAYLOAD_IN - this is the Payload file that will be in the downloaded notification .zip file RECEIVED_ENCRYPTED_AES_IV_IN - this is the Key file that will be in the downloaded notification .zip file, 000000.00000.TA.840_Key for example DECRYPTED_PAYLOAD_OUT - this is the name of the decrypted output file
#!/bin/bash
#
# @author Subir Paul (IT:ES:SE:PE)
#
#
SCRIPT=$0
function usage {
printf 'Usage: %s -privatekey <receiver private key pem input file> -in <cipher text input file> [-aeskeyiv <encrypted aes+iv input file>] [-out <plain text output file>]\n' $SCRIPT
exit 1
}
# Reset all variables that might be set
INFILE=
OUTFILE=
PRIVATEKEY=
AESKEYIV=
# Read command line args
while :; do
case $1 in
-h|--help)
usage
;;
-in|--in)
if [ -n "$2" ]; then
INFILE=$2
shift
else
printf 'ERROR: "-in" requires a non-empty option argument.\n' >&2
exit 1
fi
;;
-aeskeyiv|--aeskeyiv)
if [ -n "$2" ]; then
AESKEYIV=$2
shift
else
printf 'ERROR: "-aeskeyiv" requires a non-empty option argument.\n' >&2
exit 1
fi
;;
-privatekey|--privatekey)
if [ -n "$2" ]; then
PRIVATEKEY=$2
shift
else
printf 'ERROR: "-privatekey" requires a non-empty option argument.\n' >&2
exit 1
fi
;;
-out|--out)
if [ -n "$2" ]; then
OUTFILE=$2
shift
fi
;;
--) # End of all options.
shift
break
;;
-?*)
printf 'WARN: Unknown option (ignored): %s\n' "$1" >&2
;;
*) # Default case: If no more options then break out of the loop.
break
esac
shift
done
if [ -z "$PRIVATEKEY" ]; then
printf 'missing -privatekey <receiver private key pem input file>\n'
usage
fi
if [ ! -f $PRIVATEKEY ]; then
printf 'missing receiver private key pem input file %s\n' $PRIVATEKEY
exit 1
fi
if [ -z "$INFILE" ]; then
printf 'missing -in <cipher text input file>\n'
usage
fi
if [ ! -f $INFILE ]; then
printf 'missing cipher text input file %s\n' $INFILE
exit 1
fi
if [ -z "$AESKEYIV" ]; then
printf 'missing -aeskeyiv <encrypted aes+iv input file>\n'
usage
fi
if [ ! -f $AESKEYIV ]; then
printf 'missing encrypted aes+iv input file %s\n' $AESKEYIV
exit 1
fi
if [ -z "$OUTFILE" ]; then
OUTFILE=`echo $INFILE.out`
fi
echo "privatekey=$PRIVATEKEY infile=$INFILE aeskeyiv=$AESKEYIV outfile=$OUTFILE"
# Decrypt encrypted AESKEY+IV using receiver's RSA PKI private key
TMP=`openssl rsautl -decrypt -in $AESKEYIV -inkey $PRIVATEKEY | perl -pe '$_=unpack("H*",$_)'`
# Extract 32 bytes AESKEY and 16 bytes IV
AESKEY2DECRYPT=`echo ${TMP:0:64}`
IV2DECRYPT=`echo ${TMP:64:96}`
# Decrypt payload using D_AESKEY and D_IV
openssl enc -d -aes-256-cbc -in $INFILE -out $OUTFILE -K $AESKEY2DECRYPT -iv $IV2DECRYPT
# Check if OUTFILE are created
if [ -f $OUTFILE ]; then
echo "Plain text payload file=$OUTFILE created"
fi
CBC - Linux Sample Script
An example of running the encrypt and decrypt scripts with the required parameters:
#!/bin/bash
#
# @author Subir Paul (IT:ES:SE:PE)
#
#
RECEIVER_PUBLIC_KEY=ReceiverPublicKey.pem
SENDER_PAYLOAD_IN=Sample_000000.00000.TA.124_Payload.signed.xml
ENCRYPTED_PAYLOAD_TO_SEND_OUT=000000.00000.TA.124_Payload
ENCRYPTED_AES_IV_TO_SEND_OUT=000000.00000.TA.840_Key
# Usage: ./encrypt.sh" -pubkey <receiver public key PEM file> -in <plain text file> [-aeskeyiv <encrypted aeskeyiv file>] [-out <cipher text file>
./encrypt.sh -pubkey $RECEIVER_PUBLIC_KEY -in $SENDER_PAYLOAD_IN -aeskeyiv $ENCRYPTED_AES_IV_TO_SEND_OUT -out $ENCRYPTED_PAYLOAD_TO_SEND_OUT
RECEIVER_PRIVATE_KEY=ReceiverPrivateKey.pem
RECEIVED_ENCRYPTED_PAYLOAD_IN=000000.00000.TA.124_Payload
RECEIVED_ENCRYPTED_AES_IV_IN=000000.00000.TA.840_Key
DECRYPTED_PAYLOAD_OUT=000000.00000.TA.124_Payload.decrypted.xml
# Usage: ./decrypt.sh" -privatekey <receiver private key PEM file> -in <cipher text file> [-aeskeyiv <encrypted aes+iv file>] [-out <plain text file>]
./decrypt.sh -in $RECEIVED_ENCRYPTED_PAYLOAD_IN -privatekey $RECEIVER_PRIVATE_KEY -aeskeyiv $RECEIVED_ENCRYPTED_AES_IV_IN -out $DECRYPTED_PAYLOAD_OUT
CBC - Manual OpenSSL Commands for Encryption and Decryption
If you are having trouble with an automated method above, there are additional steps you can take to encrypt or decrypt the AES key, manually get the required hex key data, and use it to decrypt the Payload file.
Creating the AES Key and IV:
A random 48 byte value will be created and a hex version will also be created. Both the binary and hex values will be used.
The following code should be run in the same folder as the openssl executable and necessary files.
openssl rand 48 > 48byterandomvalue.bin
hexdump /bare 48byterandomvalue.bin > 48byterandomvalue.txt
Creating the random 48 byte value:
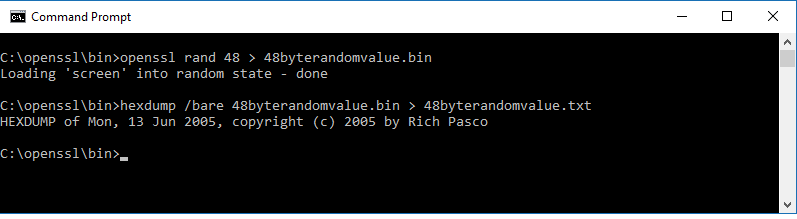 Figure 2
Figure 2
The hexdump flag in the command above will output the key in hexadecimal format which is needed to decrypt the Payload file. However, there is extra information that is included that needs to be removed before it can be used in the next command. You can use a text editor to open the 48byterandomvalue.txt file which is the output of the first command.
Example Hex data in Notepad++:
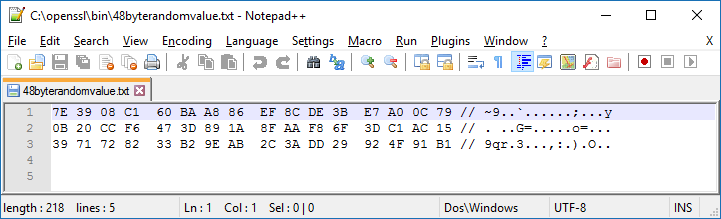 Figure 3
Figure 3
Example Hex data in Notepad:
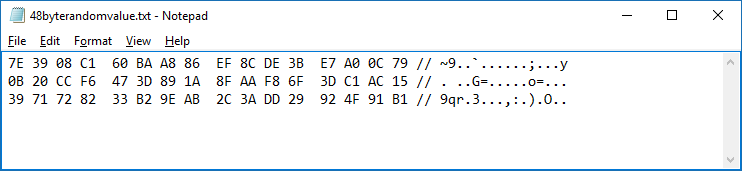 Figure 4
Figure 4
The first two lines will become the AES key and the third line will become the IV. The hex content that is needed from the file is bolded below. The rest of the information needs to be removed.
7E 39 08 C1 60 BA A8 86 EF 8C DE 3B E7 A0 0C 79 // ~9..`......;...y
0B 20 CC F6 47 3D 89 1A 8F AA F8 6F 3D C1 AC 15 // . ..G=.....o=...
39 71 72 82 33 B2 9E AB 2C 3A DD 29 92 4F 91 B1 // 9qr.3...,:.).O..
- With the spaces and dashes removed and leftover characters together, the end result is a 64 character string and a 32 character string. The first string must be exactly 64 characters in length and will be the AES key. The second string must be exactly 32 characters in length and will be the IV.
7E3908C160BAA886EF8CDE3BE7A00C790B20CCF6473D891A8FAAF86F3DC1AC15
3971728233B29EAB2C3ADD29924F91B1
The first command to encrypt the Payload file can then be executed using the AES and IV hex values. The Payload file to be encrypted is needed as well as the two hex values.
openssl aes-256-cbc -e -in PAYLOAD.zip -out PAYLOAD -K 7E3908C160BAA886EF8CDE3BE7A00C790B20CCF6473D891A8FAAF86F3DC1AC15 -iv 3971728233B29EAB2C3ADD29924F91B1
Encrypting the Payload file:
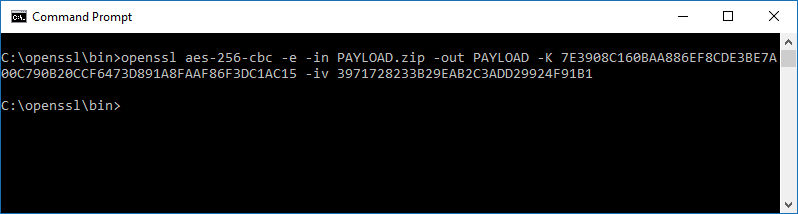 Figure 5
Figure 5
The second command to encrypt the 48 byte AES key and IV file can then be executed. This will use the initial 48 byte binary file that was created as well as the receiver's public key.
openssl rsautl -encrypt -certin -inkey cbctest_public.pem -in 48byterandomvalue.bin -out 000000.00000.TA.840_Key
Encrypting the Payload file:
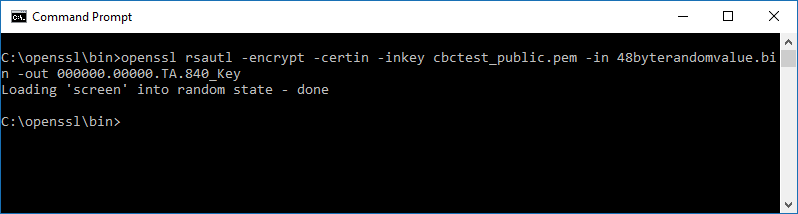 Figure 5
Figure 5
The end result of these two commands are the encrypted Payload and Key files needed for the IDES data packet.
Decrypting the AES key file:
openssl rsautl -decrypt -hexdump -in 000000.00000.TA.840_Key -inkey cbctest_private.pem -out aeskeyandiv.txt
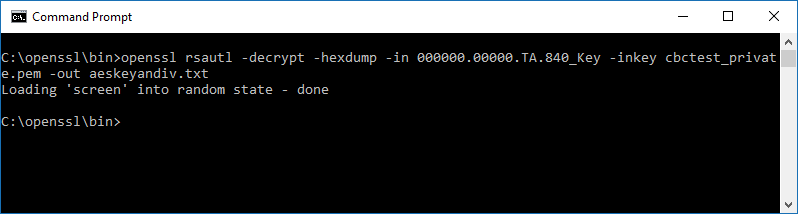 Figure 6
Figure 6
The hexdump flag in the command above will output the key in hexadecimal format which is needed to decrypt the Payload file. However, there is extra information that is included that needs to be removed before it can be used in the next command. You can use a text editor to open the aeskeyandiv.txt file which is the output of the first command.
Example Hex data in Notepad++:
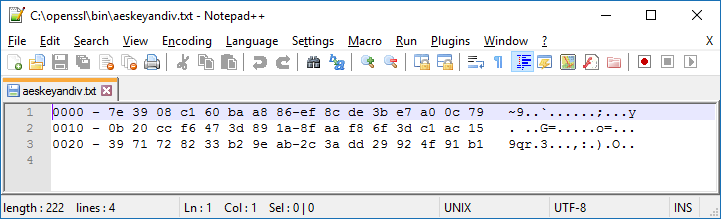 Figure 7
Figure 7
There are three lines in the file. The first two are the AES key and the third is the IV. The hex content that is needed from the file is bolded below. The rest of the information needs to be removed.
0000 - 7e 39 08 c1 60 ba a8 86-ef 8c de 3b e7 a0 0c 79 ~9..`......;...y
0010 - 0b 20 cc f6 47 3d 89 1a-8f aa f8 6f 3d c1 ac 15 . ..G=.....o=...
0020 - 39 71 72 82 33 b2 9e ab-2c 3a dd 29 92 4f 91 b1 9qr.3...,:.).O..
- With the beginning and ending information stripped out.
7e 39 08 c1 60 ba a8 86-ef 8c de 3b e7 a0 0c 79
0b 20 cc f6 47 3d 89 1a-8f aa f8 6f 3d c1 ac 15
39 71 72 82 33 b2 9e ab-2c 3a dd 29 92 4f 91 b1
- With the spaces and dashes removed and leftover characters together, the end result is a 64 character string and a 32 character string. The first string must be exactly 64 characters in length and will be the AES key. The second string must be exactly 32 characters in length and will be the IV.
7E3908C160BAA886EF8CDE3BE7A00C790B20CCF6473D891A8FAAF86F3DC1AC15
3971728233B29EAB2C3ADD29924F91B1
The second command to decrypt the Payload file can then be executed using the AES key and the IV. The Payload file from the downloaded notification zip file is needed as well as the 64 character hex key string (AES key) and 32 character hex string (IV).
openssl aes-256-cbc -d -in PAYLOAD -out PAYLOADOUT.zip -K 7E3908C160BAA886EF8CDE3BE7A00C790B20CCF6473D891A8FAAF86F3DC1AC15 -iv 3971728233B29EAB2C3ADD29924F91B1
Decrypting the Payload file:
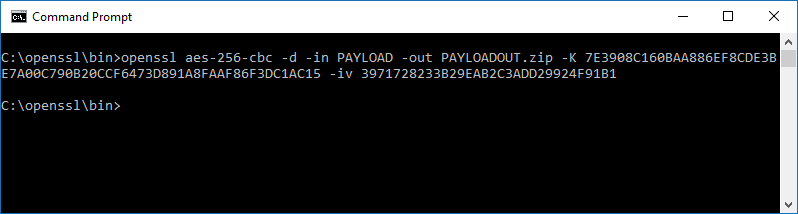 Figure 8
Figure 8
This will decrypt the encrypted Payload file giving you the zip file which contains the XML Payload file.
Folder Contents with the Payload .zip file:
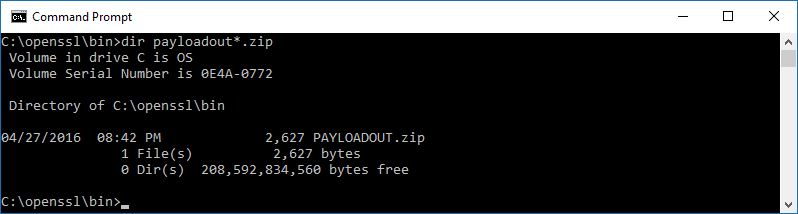 Figure 9
Figure 9
The decrypted .zip file contains the Payload file:
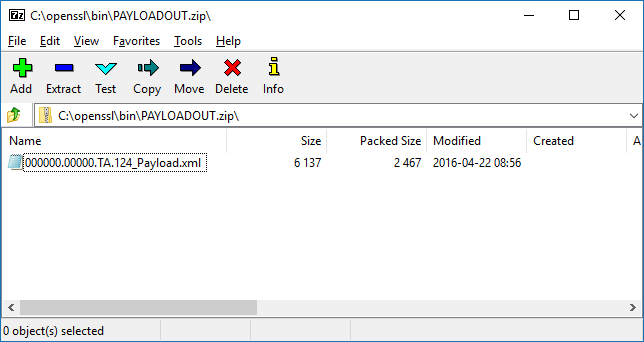 Figure 10
Figure 10
PLEASE NOTE: THE FOLLOWING SAMPLES ARE FOR ECB DECRYPTION ONLY. THESE ARE PROVIDED FOR LEGACY DECRYPTION AND WILL NOT BE COMPATIBLE WITH IDES AFTER JULY 9, 2016.
ECB Decryption - Windows Batch Scripting
The following code should be placed into a batch file and run in the same folder as the openssl executable.
The following files are required and the filename in the batch script will need to be replaced with your filename for each:
KEYFILE - this is the Key file that will be in the downloaded notification .zip file
PRIVATEKEY - this will be your private key that corresponds to the certificate that was uploaded into IDES
PAYLOAD - this is the Payload file that will be in the downloaded notification .zip file
The first command will decrypt the AES key. The batch code will parse the hex values of the AES key and prepare it for the second command. The second command will use the AES key in hex format and decrypt the Payload file. The output will be the decrypted Payload .zip file.
openssl rsautl -decrypt -hexdump -in KEYFILE -inkey PRIVATEKEY -out aeskey.txt
set /p firstline=< aeskey.txt
Set line1=%firstline%
set result1=%line1:~7,48%
Setlocal EnableDelayedExpansion
for /f "tokens=* delims= " %%i in (aeskey.txt) do (
set var=%%i
)
set result2=!var:~7,48!
set result1=%result1: =%
set result1=%result1:-=%
set result1=%result1:~0,32%
set result2=%result2: =%
set result2=%result2:-=%
set result2=%result2:~0,32%
set combined=%result1%%result2%
openssl aes-256-ecb -d -in PAYLOAD -out PAYLOAD.zip -K %combined%
Running the batch file:
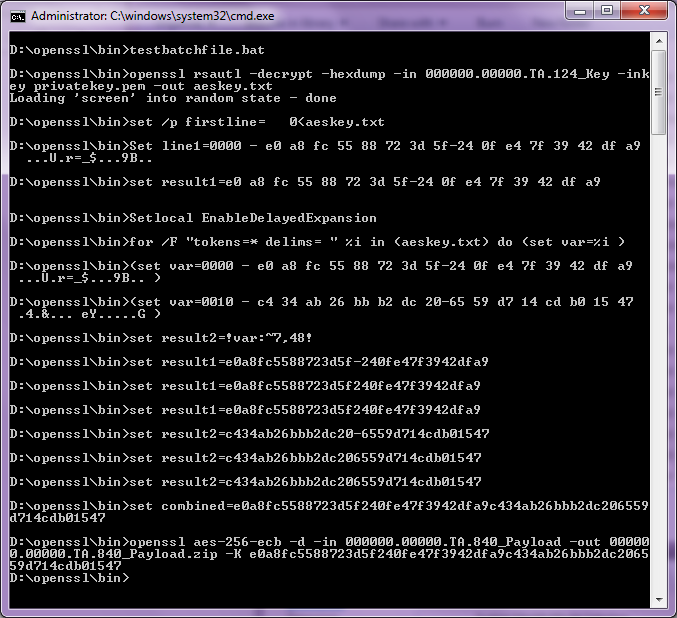 Figure 11
Figure 11
ECB Decryption - Linux Shell Scripting
Similar to the Windows method above, the following code should be placed into a shell script and run in the same folder as the openssl executable. However, this script will use the cut command to prepare the hex data.
The following files are required and the file names passed to the batch script will need to be replaced with your filename for each:
private_key - this will be your private key that corresponds to the certificate that was uploaded into IDES
key_file - this is the Key file that will be in the downloaded notification .zip file
payload_file - this is the Payload file that will be in the downloaded notification .zip file
private_key=$1 #this will be your private key that corresponds to the certificate that was uploaded into IDES
key_file=$2 #this is the Key file that will be in the downloaded notification .zip file
payload_file=$3 #this is the Payload file that will be in the downloaded notification .zip file
output_file=$4 #this is the expected output filename, and will be in a .zip format
hexvalue='openssl rsautl -decrypt -hexdump -inkey $private_key_file -in $random_key_file|cut -c-55|cut -c7-55|tr -d "\n"|sed 's/[ -]//g' ';
openssl enc -d -aes-256-ecb -in $payload_file -out $output_file -K $hexvalue
An example of running the script with the required parameters:
decrypt.sh privatekey.pem 000000.00000.TA.124_Key 000000.00000.TA.840_Payload 000000.00000.TA.840_Payload.zip
ECB Decryption - Manual OpenSSL Commands
If you are having trouble with an automated method above, there are additional steps you can take to decrypt the AES key, manually get the required hex key data, and use it to decrypt the Payload file.
The process is similar to the automated method above. The following files are required and the filename in the batch script will need to be replaced with your filename for each:
KEYFILE - this is the Key file that will be in the downloaded notification .zip file
PRIVATEKEY - this will be your private key that corresponds to the certificate that was uploaded into IDES
PAYLOAD - this is the Payload file that will be in the downloaded notification .zip file
The following code should be run in the same folder as the openssl executable and necessary files.
Decrypting the AES key:
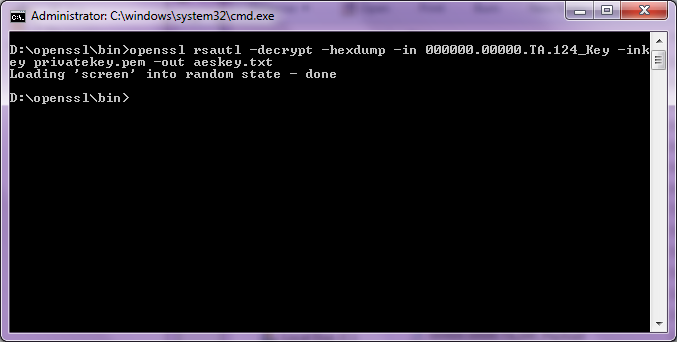 Figure 12
Figure 12
The hexdump flag in the command above will output the key in hexadecimal format which is needed to decrypt the Payload file. However, there is extra information that is included that needs to be removed before it can be used in the next command. You can use a text editor to open the aeskey.txt file which is the output of the first command.
Example Hex data in Notepad++:
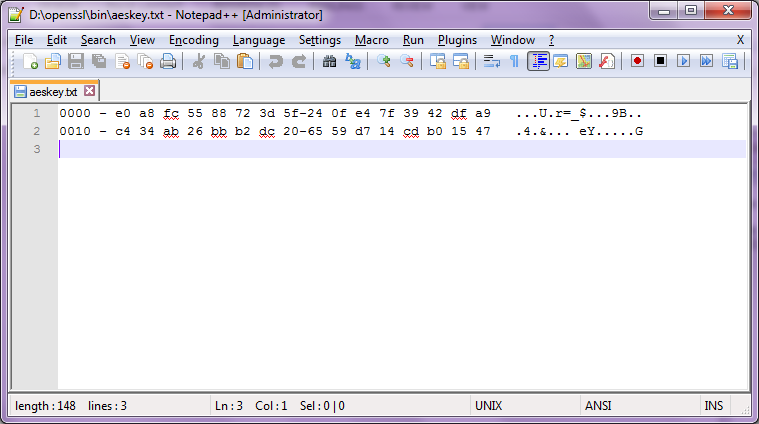 Figure 13
Figure 13
Example Hex data in Notepad:
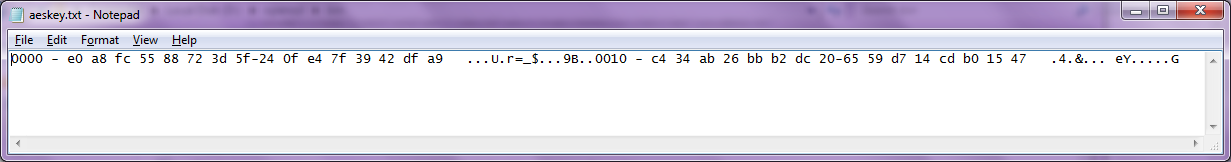 Figure 14
Figure 14
The hex content that is needed from the file is bolded below. The rest of the information needs to be removed.
0000 - e0 a8 fc 55 88 72 3d 5f-24 0f e4 7f 39 42 df a9 ...U.r=_$...9B..
0010 - c4 34 ab 26 bb b2 dc 20-65 59 d7 14 cd b0 15 47 .4.&... eY.....G
- With the beginning and ending information stripped out.
e0 a8 fc 55 88 72 3d 5f-24 0f e4 7f 39 42 df a9
c4 34 ab 26 bb b2 dc 20-65 59 d7 14 cd b0 15 47
- With the spaces and dashes removed and leftover characters together, the end result is a 64 character string. The string must be exactly 64 characters in length:
e0a8fc5588723d5f240fe47f3942dfa9c434ab26bbb2dc206559d714cdb01547
The second command to decrypt the Payload file can then be executed using the 64 character hex key string. The Payload file from the downloaded notification zip file is needed as well as the 64 character hex key string.
openssl aes-256-ecb -d -in 000000.00000.TA.840_Payload -out 000000.00000.TA.840_Payload.zip -K e0a8fc5588723d5f240fe47f3942dfa9c434ab26bbb2dc206559d714cdb01547
Decrypting the Payload file:
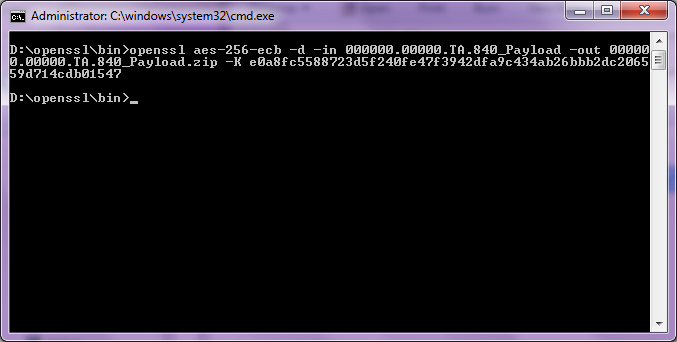 Figure 15
Figure 15
This will decrypt the encrypted Payload file giving you the zip file which contains the XML Payload file.
Folder Contents with the Payload .zip file:
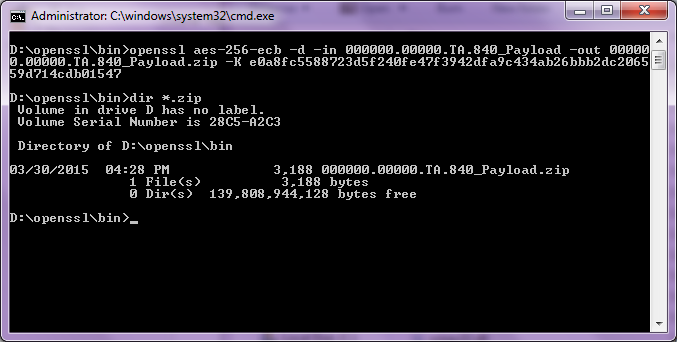 Figure 16
Figure 16
Disclaimer:
We waive copyright and related rights in the work worldwide through the CC0 1.0 Universal public domain dedication. Unless expressly stated otherwise, the person who associated a work with this deed makes no warranties about the work, and disclaims liability for all uses of the work, to the fullest extent permitted by applicable law. When using or citing the work, you should not imply endorsement by the author or the affirmer.